Existing certificate
Using an existing SSL certificate with MistServer
If you already have a certificate generated you can use this within MistServer as well. Though this is not the recommended method of enabling SSL, simply because this usually means the certificate will not automatically update. We would recommend using Certbot instead in this case or a reverse proxy if you're running MistServer adjacent to a web server.
Add HTTPS(HTTP+TLS) protocol
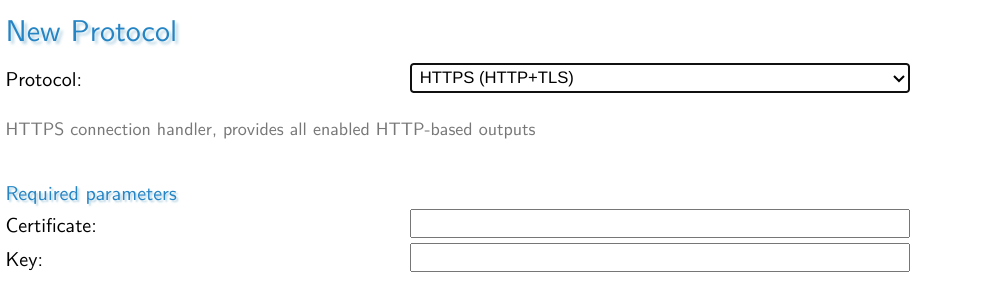
All you need to do is add the path to the certificate and key to set up HTTPS. You do not post the actual key or certificate here.
MistServer requires the certificate and key in separate formats. This means that if you have a mixed format .pfx you will have to grab your .crt and .key files out of it.
Multiple formats should be supported, but we recommend the converting your pfx to pem format should your existing one not work. IBM offers an excellent guide to do this here.
This can be easily done through openSSL using:
openssl rsa -in certificate.pfx -outform PEM -out certificate-pem.key
Pem formats follow an very easy structure. Keys should start with:
-----BEGIN RSA PRIVATE KEY-----
KEYDATA
-----END RSA PRIVATE KEY-----
Certificates should start with:
-----BEGIN CERTIFICATE-----
CERTIFICATE DATA
-----END CERTIFICATE-----
Default port is 4433
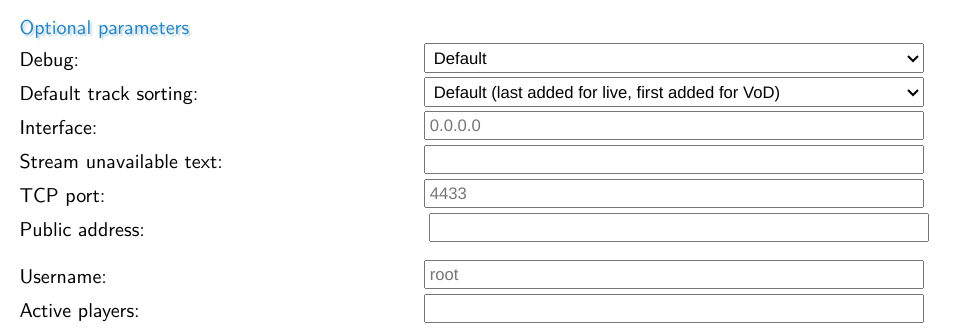
Note that the default port for HTTPS is 4433 within MistServer. This non-default HTTPS port is chosen as it is assumed that if you use this method you already have an existing certificate. You would only have one if you're running an webserver next to it, thus already using the HTTPS default port 443.